Car thieves have gone high-tech. In 2025, the same keyless entry systems that make life convenient for drivers have become a goldmine for criminals. Armed with cheap relay devices and a bit of know-how, thieves can capture and amplify your fob’s signal—even if it’s inside your house—and drive away in seconds.
Recent academic research confirms: remote keyless entry is now a main attack vector, and most automakers haven’t kept up with the threat. Attacks like relay, replay, and even cryptanalytic hacks let criminals bypass security on everything from family sedans to luxury EVs.
How It Works
- Relay Attacks: Thieves use radio amplifiers to trick your car into thinking the key is nearby—even if it’s inside your home.
- Replay/Jamming: Attackers block your unlock signal, record it, and use it later to open your car.
- Cryptanalytic Attacks: Hackers can clone keys by intercepting and analyzing the digital handshake between car and fob.
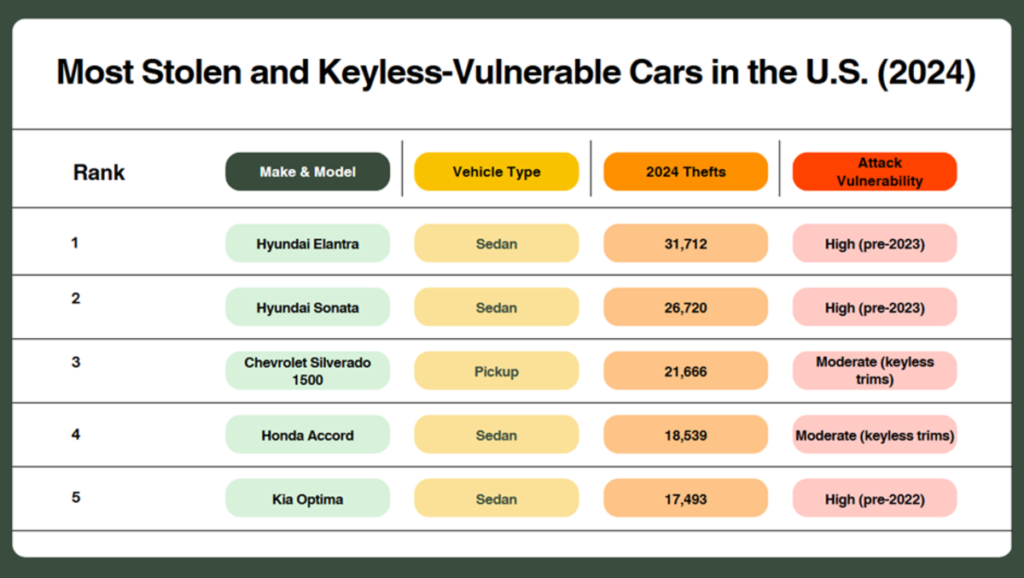
Most Vulnerable Cars in the U.S. (2024–2025)
The U.S. car theft landscape is dominated by models with weak immobilizer systems, especially older Hyundais and Kias, but modern keyless entry vulnerabilities—including those in Tesla and other brands—are a growing concern. Here are the US’ 2024 Top 10 Most Stolen from keyless entry attacks.
Tesla and Keyless Theft
- Tesla Model 3 and Model Y have been proven susceptible to Bluetooth Low Energy (BLE) relay attacks, allowing thieves to unlock and drive away in seconds if advanced security features (like PIN-to-drive) are not enabled.
- While not among the top 10 most stolen cars by volume, Tesla’s vulnerability is notable because the attack exploits the convenience of phone-as-key and BLE fobs, similar to attacks on other brands using BLE for entry/start.
- PIN-to-drive: This Tesla feature can thwart drive-away thefts, but it must be manually enabled by the owner.
Key Trends and Takeaways
- Hyundai and Kia (pre-2022/2023): Most vulnerable overall due to lack of immobilizers; relay and physical attacks are both common.
- American pickups (Chevrolet Silverado, Ford F-150): Targeted for parts and theft, with keyless entry increasing risk in newer trims.
- Other keyless models (Toyota Camry, Dodge Charger, Honda Accord/Civic): Newer trims with push-button start are susceptible to relay attacks, though immobilizers are generally present.
- Tesla and other BLE/NFC-based vehicles: Vulnerable to advanced relay attacks, especially if owners do not use additional security features.
Why Are Automakers Still Behind?
Despite years of warnings, most manufacturers have stuck with outdated cryptography and unidirectional signals. “Security by obscurity” (hoping hackers won’t find the flaws) still rules, even as researchers and thieves race to outsmart each other. The result: a boom in thefts, and a booming business for aftermarket Faraday pouches that block radio signals—because your $60,000 SUV apparently needs a $10 shield the maker won’t fork out for.
What Can Actually Stop This?
Some researchers are pushing for smarter solutions: adaptive frequency-hopping, two-way authentication protocols, and dynamic cryptographic keys. These upgrades would make it much harder for thieves to intercept or spoof signals. But until automakers make these standard, your car’s digital handshake is a handshake with risk.
Is Convenience Worth the Cost?
If your car unlocks with a wave or a ping, it’s at risk. Until the industry catches up, use all available security features, and consider a Faraday pouch or steering lock. Convenience shouldn’t mean handing your keys to a thief.